Jamming and Anti-Jamming: Protecting fleets against blockers
The war against organized crime in logistics hinges on controlling radio frequencies. Understand how to protect your operation against the use of jammers and ensure the continuity of the trail.
What is Jamming: The Physics of Signal Blocking
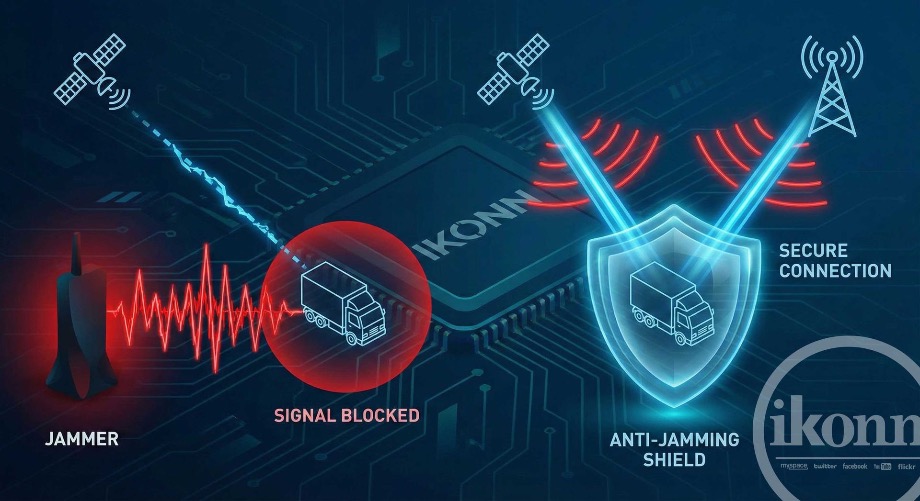
Jamming is a deliberate interference technique that uses devices known as "jammers" or "devils" to saturate communication and location frequencies. By emitting high-power white noise on the GPS (1575.42 MHz) and GSM/GPRS bands, the criminal creates an invisible barrier that prevents the tracker from receiving satellite signals or transmitting data to the central monitoring station. For those who value keeping everything in pristine condition and functioning perfectly, understanding this vulnerability is the first step towards resilience.
Although simple in concept, jamming is extremely effective. It "deafens" the hardware, causing the vehicle to disappear from the map at the exact moment of the incident. At Ikonn, our engineering approach focuses on transforming this "blindness" into an intelligence trigger, using the communication failure itself as confirmation of an attack.
Jamming Detection: Intelligence in Hardware
A robust anti-jamming system doesn't try to "win" interference by force, but rather by logic. High-tech trackers supported by Ikonn have electromagnetic noise detection algorithms. When the radio module detects an abnormal signal density in the GPS frequency, the hardware interprets this as a jamming attempt.
The technical advantage lies in what the equipment does next. Through automation and the Rules Engine , it's possible to configure the hardware to make autonomous decisions even without internet access: immediate vehicle immobilization, siren activation, or cargo compartment locking. This technical independence ensures that the digital trail is protected by the asset's own intelligence, even before the total loss of connection.
Anti-Jamming Strategies at the Central Office
On the platform, preventative monitoring is done through the analysis of signal loss patterns. If a moving vehicle simultaneously loses GPS and GPRS while the engine remains running, the probability of a jamming attack is at its highest. Ikonn's rules engine automates this diagnosis, sending priority alerts to the monitoring center in milliseconds.
In addition to network detection, the use of technologies such as Dead Reckoning and inertial sensors allows the system to continue estimating the vehicle's trajectory even under GPS jamming attacks. Combining these tools with LBS verification via the operator's portal gives the control center a technical sovereignty that the criminal cannot easily neutralize.
Strategic Installation: The Invisible Layer of Defense
The effectiveness of anti-jamming begins with the physical installation. Hidden internal antennas, the use of electromagnetic shielding in critical locations, and the decentralization of communication modules make the jammer's job much more difficult. Through Ikonn University , we disseminate best installation practices to ensure that the hardware remains undetectable and resilient.
Multi-constellation equipment, which uses GPS, GLONASS, and Galileo, also offers an extra layer of protection, as a criminal would need a much more powerful jammer to take down all bands simultaneously. The pursuit of excellence in configuration is what keeps your fleet operating with unwavering security.
Conclusion: Technical Resilience as a Priority
Jamming is a constant challenge, but it's not insurmountable. With the right combination of intelligent hardware, rule engine automation, and a robust data infrastructure, your data center transforms a threat into an opportunity to demonstrate technical superiority. At Ikonn, we work to ensure you have the tools you need to protect what matters most, guaranteeing that your digital footprint is immune to market interference attempts.
IKONN SUPPORT: Cutting-edge engineering protecting your operation against the invisible.
Is your fleet technically protected against jammers?
Consult our engineering team to validate your jamming detection protocols and ensure your control panel is making the most of Ikonn automation for preventative security.